Protecting Your Home Network: Detecting Rogue Networks with LizardSystems Wi-Fi Scanner
In an era where home networks are increasingly vulnerable to cyber threats, it's crucial to take proactive steps to secure your Wi-Fi connection. One significant concern is the presence of rogue networks, which can compromise your network security and expose your personal information to malicious actors. Fortunately, with the assistance of LizardSystems Wi-Fi Scanner, you can easily detect and protect against rogue networks to ensure the safety of your home network.
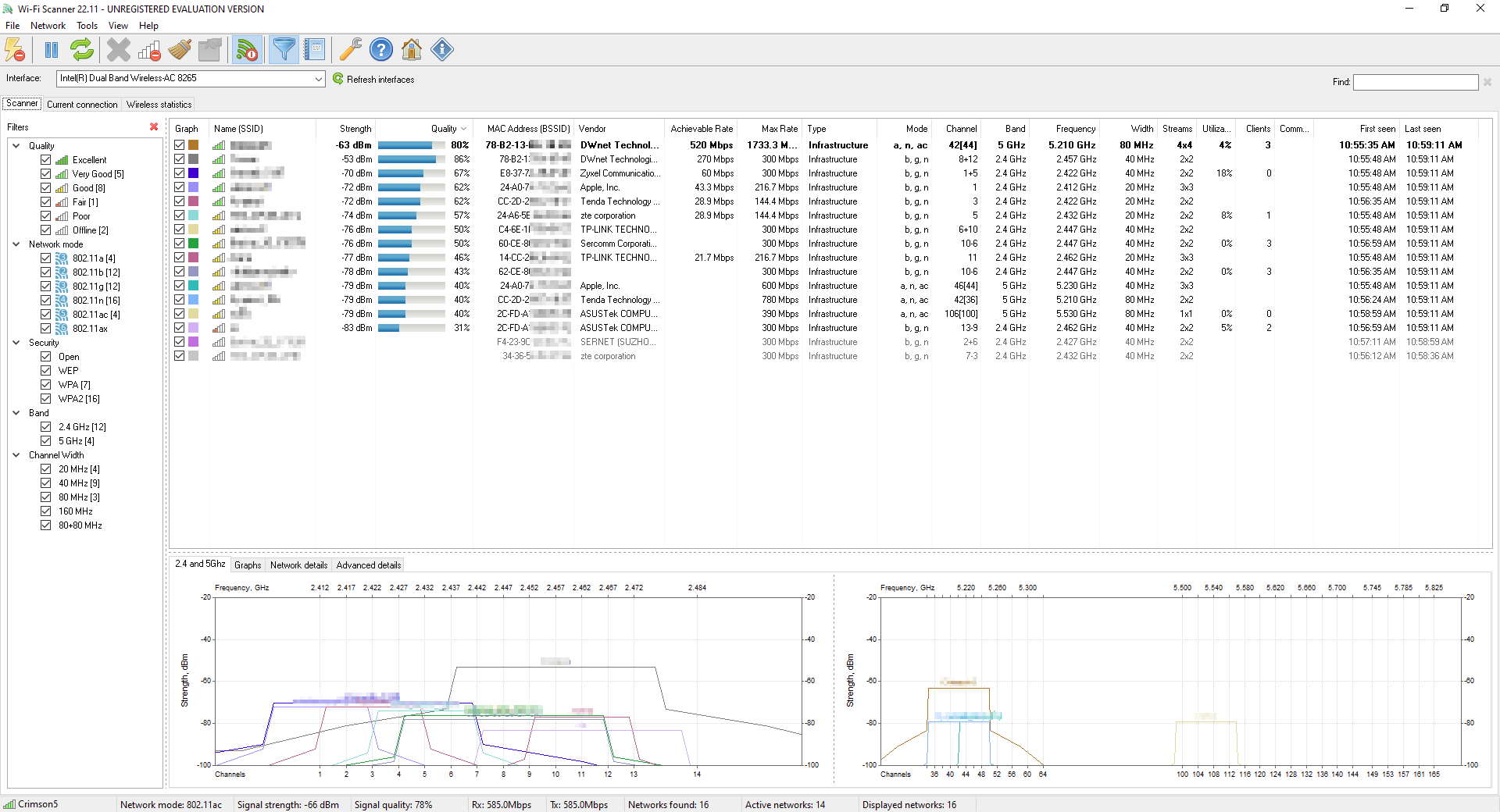
LizardSystems Wi-Fi Scanner is a reliable and user-friendly tool that provides valuable insights into the Wi-Fi networks in your vicinity. By following a few simple steps, you can identify and take action against rogue networks that may pose a risk to your home network.
Step 1: Install and Launch LizardSystems Wi-Fi Scanner
Begin by downloading and installing the LizardSystems Wi-Fi Scanner software on your computer. Once installed, launch the application to access its powerful features.
Step 2: Scan for Nearby Wi-Fi Networks
In the software interface, you'll find a list of nearby Wi-Fi networks. LizardSystems Wi-Fi Scanner displays crucial information, such as network names (SSID), signal strengths, encryption types, and MAC addresses, for each network. This information serves as the foundation for detecting rogue networks.
Step 3: Identify Suspicious Networks
Scan the list for any unfamiliar or suspicious networks that may be rogue networks. Pay attention to networks with names that don't align with expected networks in your vicinity. Rogue networks often use naming conventions that mimic legitimate networks, so be cautious and vigilant.
Step 4: Analyze Signal Strength and Channel Usage
Rogue networks may exhibit unusually high signal strengths or use the same channels as your authorized networks. These factors can impact your network performance and indicate the presence of rogue networks. Look for networks with significantly stronger signals or networks sharing channels with your authorized devices.
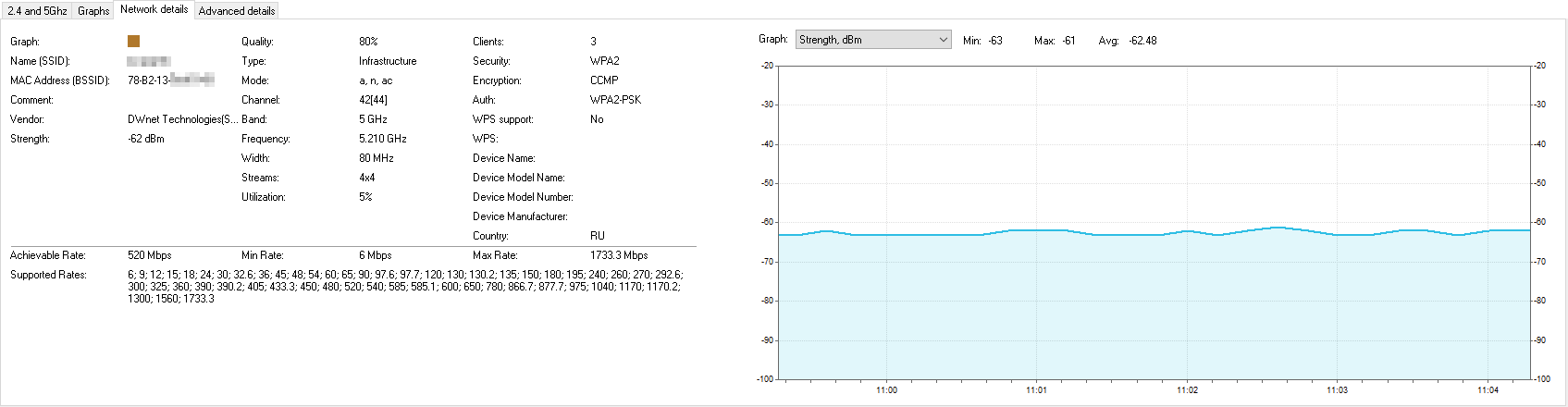
Step 5: Verify MAC Addresses
Cross-reference the MAC addresses of the detected networks with the MAC addresses of your authorized devices. Rogue networks often use different MAC addresses compared to legitimate access points. If you notice a network with an unrecognized MAC address, it may indicate a rogue network.
Step 6: Take Action
If you identify a suspicious network that you believe to be a rogue network, it's important to take immediate action. Consider changing your Wi-Fi network's password, enabling strong encryption protocols like WPA2 or WPA3, and contacting your internet service provider (ISP) for further guidance.
By following these steps and leveraging the capabilities of LizardSystems Wi-Fi Scanner, you can significantly enhance the security of your home network. Regularly scanning for rogue networks and promptly addressing any potential threats will help safeguard your personal information and ensure a safe online experience for you and your family.
Remember, securing your home network goes beyond just using Wi-Fi scanning tools. It's crucial to employ strong passwords, keep your network equipment updated with the latest firmware, and educate yourself about other essential security practices.
In conclusion, with the assistance of LizardSystems Wi-Fi Scanner, detecting rogue networks and protecting your home network has become more accessible than ever. By remaining vigilant, regularly scanning your network, and taking appropriate action against suspicious networks, you can fortify your home network's defenses and enjoy a safe and secure online environment.