How to Add Users and Grant RDP Permissions on Windows Server: A Comprehensive Guide
How to Add Users and Grant RDP Permissions on Windows Server: A Comprehensive Guide
Remote Desktop Protocol (RDP) is a cornerstone of modern IT infrastructure, enabling secure remote access to Windows Servers. However, improper configuration of RDP permissions can expose your systems to security risks or operational inefficiencies. In this guide, we’ll walk you through how to add users and configure RDP permissions step by step, while highlighting how LizardSystems Terminal Services Manager simplifies and enhances this process.
Why Proper RDP Permissions Matter
Before diving into the steps, let’s address why RDP permissions are critical:
-
Security: Unauthorized RDP access is a common attack vector for breaches.
-
Compliance: Many regulations (e.g., GDPR, HIPAA) require strict access controls.
-
Performance: Overloaded servers due to unrestricted access can degrade user experience.
Tools like Terminal Services Manager help enforce these permissions while providing real-time monitoring and auditing capabilities.
Step 1: Enable Remote Desktop on Windows Server
Manual Method:
-
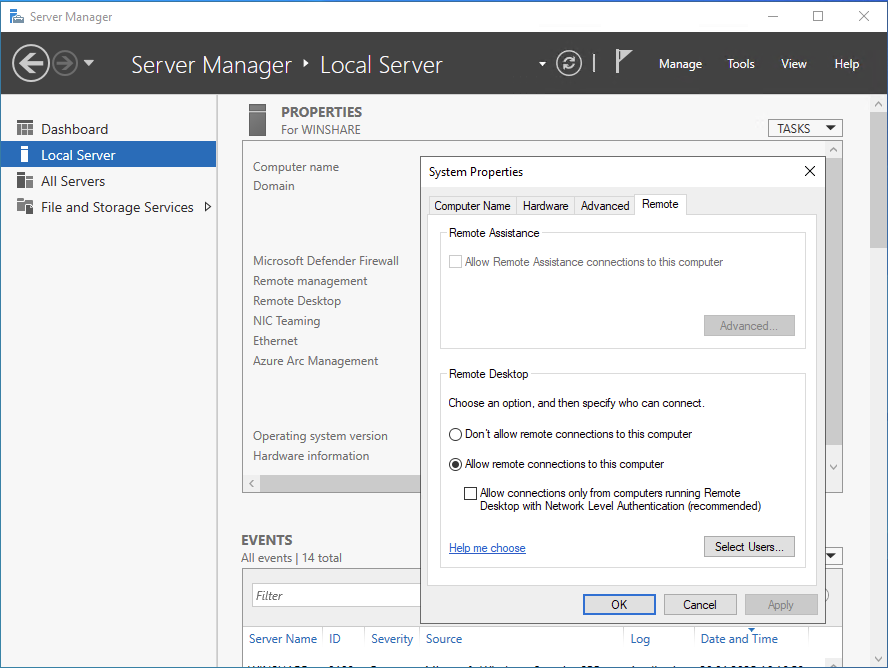
Open Server Manager → Local Server → Remote Desktop.
-
Select Allow remote connections to this computer.
-
Enable Network Level Authentication (NLA) for enhanced security.
PowerShell Script:
# Enable RDP and NLA Set-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\Terminal Server" -Name "fDenyTSConnections" -Value 0 Set-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" -Name "UserAuthentication" -Value 1
Pro Tip: Use Terminal Services Manager to monitor RDP status across multiple servers from a single dashboard.
Step 2: Add Users to the Remote Desktop Users Group
Manual Method:
-
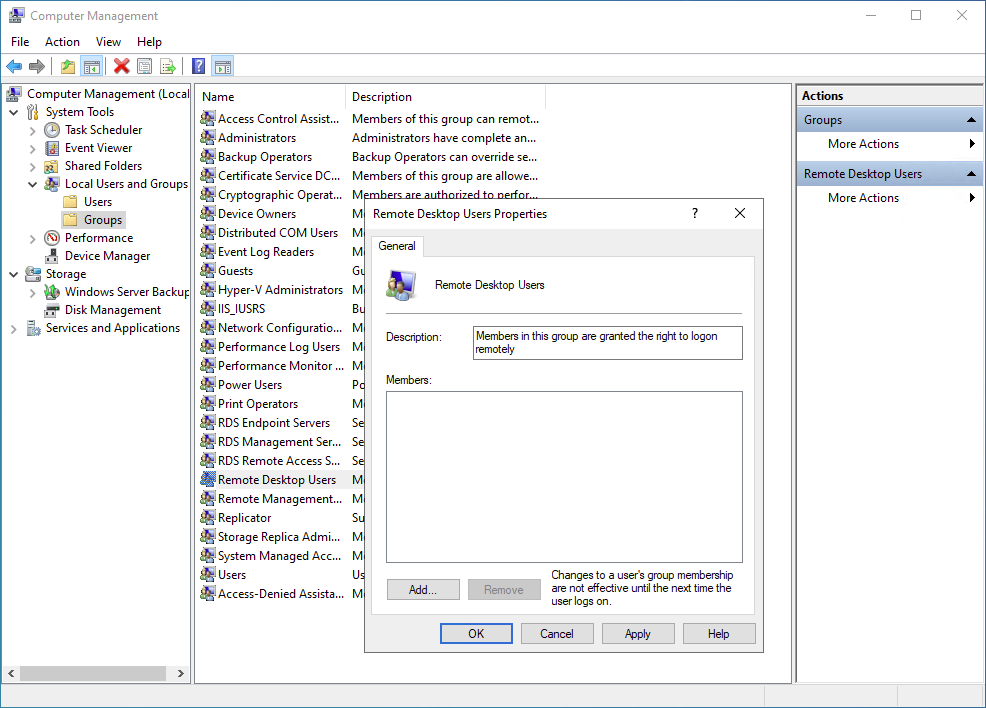
Open Computer Management → Local Users and Groups → Groups.
-
Double-click Remote Desktop Users → Add → Enter the username (e.g., DOMAIN\User1).
PowerShell Script:
# Add a user to the Remote Desktop Users group Add-LocalGroupMember -Group "Remote Desktop Users" -Member "User1"
Why This Matters: Restricting RDP access to specific users minimizes exposure to credential-based attacks.
Step 3: Advanced Configuration with Group Policy (Optional)
Manual Method:
For enterprise environments, use Group Policy to enforce RDP permissions:
-
Open Group Policy Management Console (GPMC).
-
Create a GPO → Navigate to Computer Configuration → Policies → Windows Settings → Security Settings → User Rights Assignment.
-
Edit Allow log on through Remote Desktop Services → Add users/groups.
PowerShell Script:
# Create a GPO to grant RDP access New-GPO -Name "RDP Access Policy" Set-GPPermission -Name "RDP Access Policy" -TargetName "DOMAIN\FinanceTeam" -TargetType Group -PermissionLevel GpoApply
Best Practices for Secure RDP Management
-
Enable Multi-Factor Authentication (MFA): Use tools like Azure AD Conditional Access with RDP.
-
Limit Concurrent Sessions: Prevent server overload by restricting simultaneous connections.
-
Monitor Active Sessions:
-
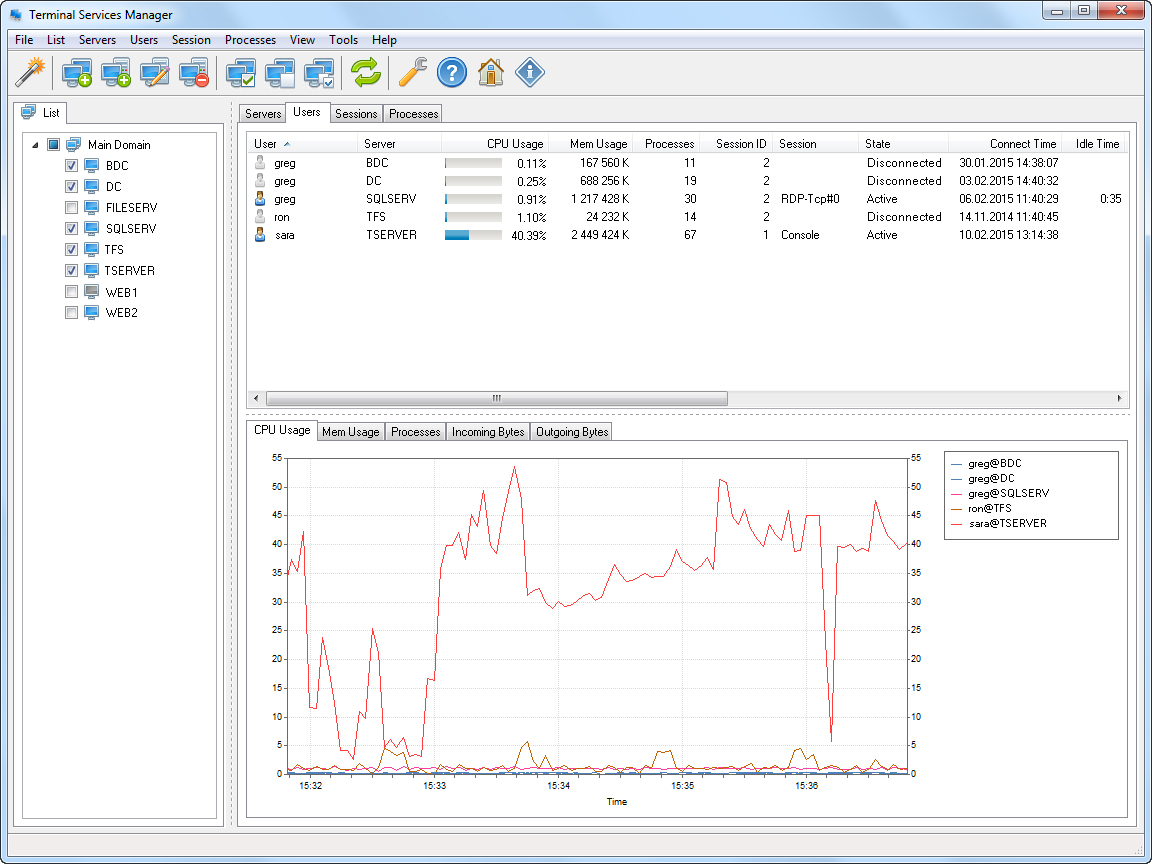
With Terminal Services Manager: View real-time sessions, identify idle users, or terminate suspicious connections.
-
PowerShell Command:
qwinsta /server:SERVER01 # List active RDP sessions
-
-
Regular Audits: Use Terminal Services Manager to generate reports on RDP access patterns.
Example Workflow: Granting Temporary RDP Access
Scenario: A contractor needs access to a server.
-
Add the User:
Add-LocalGroupMember -Group "Remote Desktop Users" -Member "Contractor01"
- Monitor Activity: Use Terminal Services Manager to track the contractor’s session duration and resource usage.
Troubleshooting Common RDP Issues
-
"User Not in Remote Desktop Users Group"
Verify group membership with:
Get-LocalGroupMember -Group "Remote Desktop Users"
-
RDP Port Blocked by Firewall
Ensure port 3389 is open (or your custom RDP port).
-
Server Overload
Use Terminal Services Manager to identify resource-heavy sessions and balance loads.
Conclusion: Streamline RDP Management with Terminal Services Manager
Configuring RDP permissions manually is error-prone and time-consuming. LizardSystems Terminal Services Manager enhances security and efficiency by:
-
Providing centralized control over RDP access.
-
Offering real-time monitoring and alerts for suspicious activity.
Ready to Optimize Your RDP Workflow?
Download Terminal Services Manager to simplify server management and enforce least-privilege access effortlessly.
Jan 28, 2025
Similar articles
- How to Protect User Sessions from Remote Viewing on Terminal Servers
- LizardSystems Terminal Services Manager: A Powerful Tool for Remote Desktop Management
- How to grant shadow access rights for users without grant full admins rights in RDS-servers?
- Troubleshooting monitoring issues for performance counters