How to grant shadow access rights for users without grant full admins rights in RDS-servers?
In Windows operating systems, shadowing allows an administrator or authorized user to view and control a user's session remotely. This feature is useful when troubleshooting issues, training new employees, or monitoring employee activity. However, granting shadowing access rights can be risky as it gives the user access to sensitive information and potentially compromises security.
To grant shadow access rights to specific users or groups and minimize security risks, follow these steps:
First, create a security group that will contain the users who need shadow access rights.
Next, navigate to the RDS server where you want to grant shadowing permissions and log in as an administrator. Open the Local Group Policy Editor by typing gpedit.msc in the Run dialog box and pressing Enter.
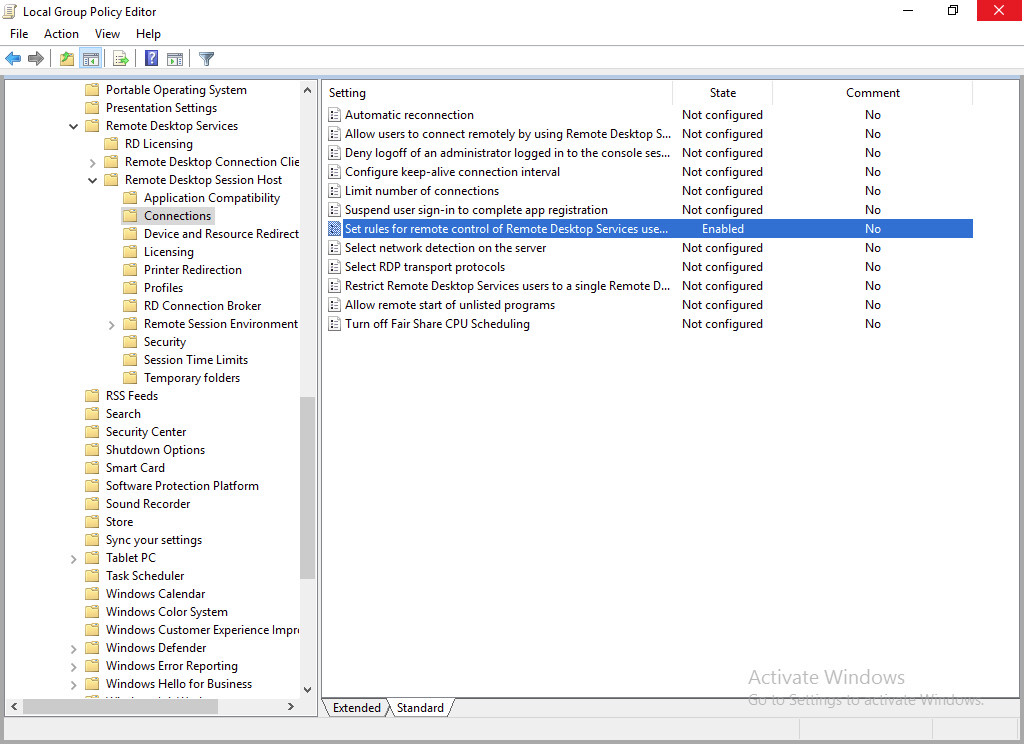
Navigate to Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections.
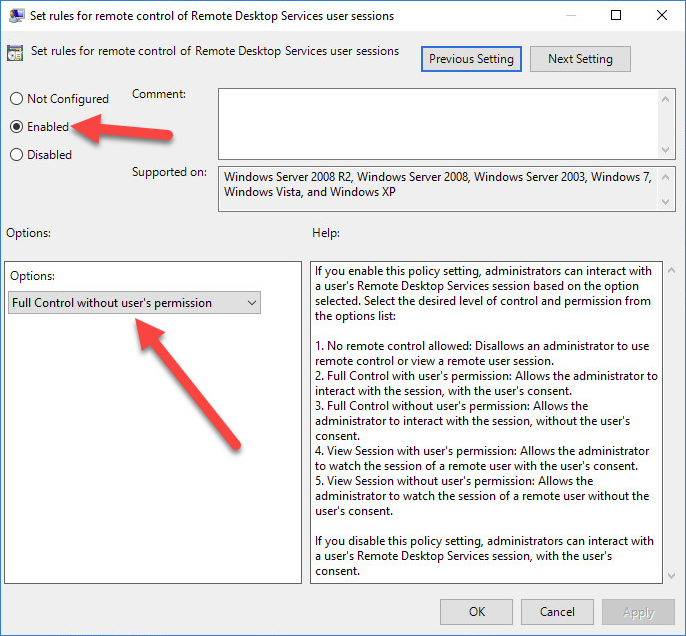
Double-click the "Set rules for remote control of Remote Desktop Services user sessions" policy setting and select Enabled. Under Options, select the "Full Control without user's permission" option.
Open a command prompt on the RDS server with administrative privileges.
Run the following command to grant non-admin users the ability to shadow RDS sessions:
wmic /namespace:\\root\CIMV2\TerminalServices PATH Win32_TSPermissionsSetting WHERE (TerminalName=”RDP-Tcp”) CALL AddAccount "DOMAIN\USER",2
To revert the permissions back to the default permissions, specify the relevant terminal name. Then, call the RestoreDefaults method.
wmic /namespace:\\root\CIMV2\TerminalServices PATH WIN32_TSPermissionsSetting.TerminalName="Console" call RestoreDefaults
After completing these steps, the non-admin user should be able to shadow RDS sessions. Note that this method grants non-admin users the ability to shadow sessions and may also grant them other administrative privileges depending on their permissions. It is recommended to test this method thoroughly before implementing it in a production environment.
To verify that the users in the security group have shadow access rights, log in as one of the users and attempt to shadow another user's session. If the shadowing feature works correctly, then the user has the necessary permissions.
Granting shadow access rights to users on Windows RDS servers can be challenging while minimizing security risks. However, by following the steps outlined in this article, you can create a security group in Active Directory, grant shadowing permissions through Local Group Policy, add users to the security group, and verify the users' shadowing access. By doing so, you can ensure that only authorized users have access to shadowing features on your RDS servers.
Apr 24, 2023