Why do you need a Monitoring Failed Logon Attempts
Monitoring failed logon attempts is an essential security practice for several reasons:
1. Intrusion detection: Failed logon attempts can indicate unauthorized access attempts or malicious activities. Monitoring these attempts helps detect potential intrusion attempts or brute-force attacks where attackers repeatedly try different username and password combinations to gain access to a system.
2. Account compromise detection: Failed logon attempts can be an early warning sign of compromised user accounts. If a user account is repeatedly targeted with failed logon attempts, it may suggest that the account credentials have been compromised and someone is trying to gain unauthorized access.
3. User behavior analysis: Monitoring failed logon attempts provides insights into user behavior patterns. It allows administrators to identify unusual login activity, such as a user attempting to log in from multiple locations simultaneously or at odd hours. This information can help identify potential insider threats or compromised user accounts.
4. Security policy assessment: Analyzing failed logon attempts can help evaluate the effectiveness of security policies and measures. For example, if a particular account consistently experiences failed logon attempts, it may indicate a weak password policy or the need for multi-factor authentication.
5. Forensic investigation: In the event of a security breach or incident, monitoring failed logon attempts becomes crucial for forensic investigations. Examining the logs can provide valuable information about the attack vectors, IP addresses, or user accounts involved, aiding in incident response and recovery efforts.
By monitoring failed logon attempts, organizations can enhance their overall security posture, promptly respond to potential threats, and proactively protect sensitive data and systems from unauthorized access.
You may view information about failed logon attempts in Terminal Services Manager.
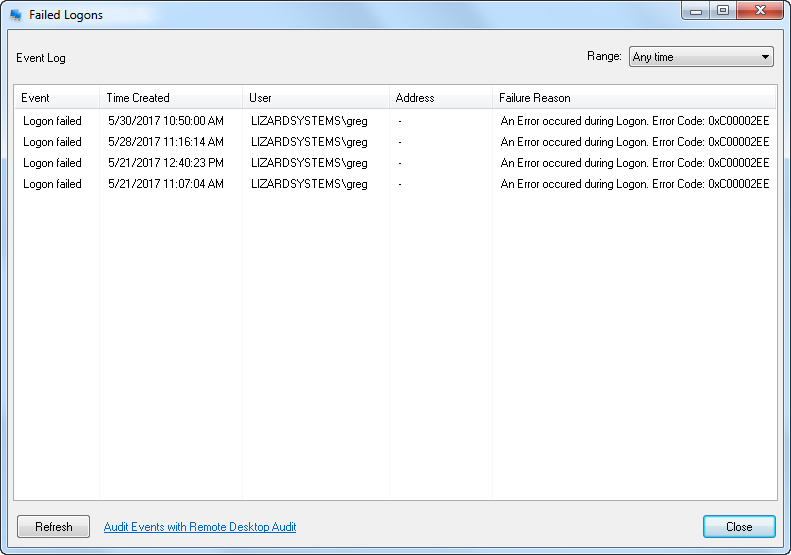
For more detailed information, you can use Remote Desktop Audit. By utilizing Remote Desktop Audit, administrators can effectively identify failed logons and other suspicious events, which frequently serve as indicators of potential hacker attacks. The tool's advanced monitoring features enable the timely detection of these security incidents, empowering administrators to take prompt action and mitigate risks effectively. Moreover, in the event of a network incident, Remote Desktop Audit proves invaluable for conducting rapid analysis and conducting thorough investigations.
May 16, 2023
Product: Terminal Services Manager Remote Desktop Services , RDS , failed logons , terminal services manager